The following was released today in relation to attacks on WordPress sites. If you do not have any security on your website then now is the time to get it!
All Websites that have a support and maintenance contract with me are already secure but if yours has no security, out of date plugins and software then you need to act now.
The Defiant Threat Intelligence team recently began tracking the behavior of an organized brute force attack campaign against WordPress sites. This campaign has created a botnet of infected WordPress websites to perform its attacks, which attempt XML-RPC authentication to other WordPress sites in order to access privileged accounts.
More than five million malicious authentication (login) attempts associated with this attack campaign have been blocked in the last thirty days alone.
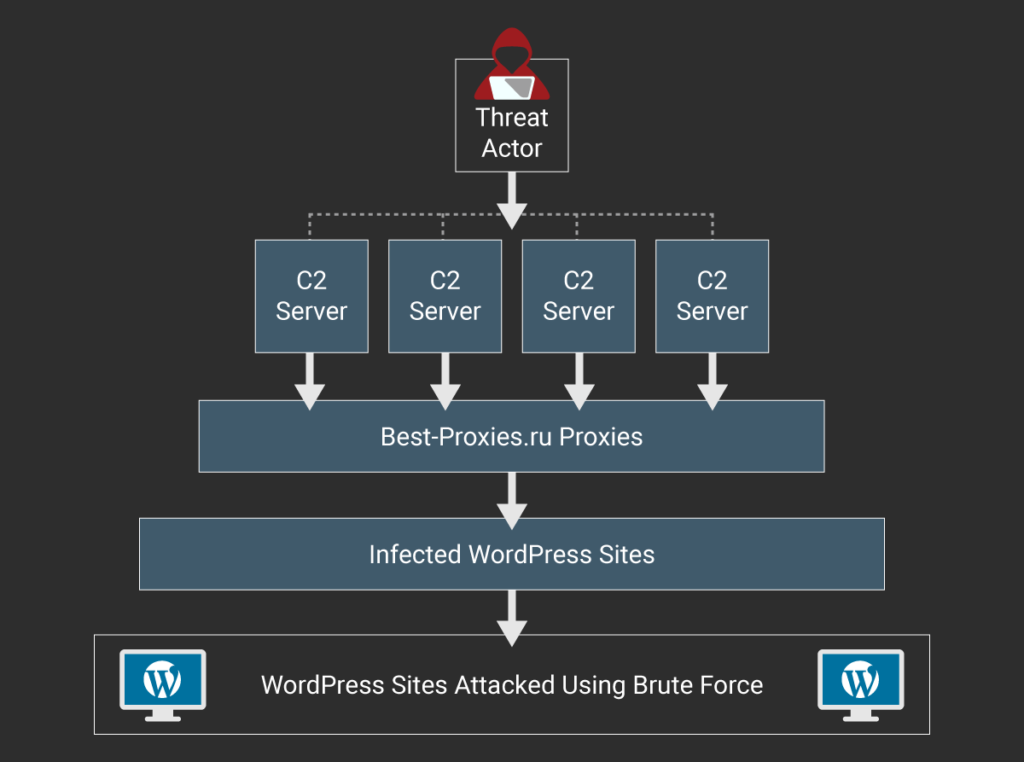
The threat actors (hackers) use a group of four command and control (C2) servers to send requests to over 14,000 proxy servers provided by a Russian proxy provider called best-proxies[.]ru. They use these proxies to anonymise the C2 traffic. The requests pass through the proxy servers and are sent to over 20,000 infected WordPress sites. Those sites are running an attack script which attacks targeted WordPress sites. The diagram below illustrates the attack chain.
What Should Site Owners Do?
In order to prevent your site from falling victim to brute force attacks, it is valuable to implement restrictions and lockouts for failed logins by installing robust brute force protection , and blocking the IPs launching the attacks.
